It is with great pleasure that today I announce the first release of Jabbercracky, the hash-cracking web service. MD5, NTLM, LM, and HalfLM are currently fully supported. Jabbercracky will only work on Linux/Posix systems.
Jabbercracky makes use of a two-pass hash cracking method. In the first pass, the submitted hash is tried against a local collection of rainbow tables. In the second pass, the hash is passed along to a Cuda-compatable GPU for brute-forcing.
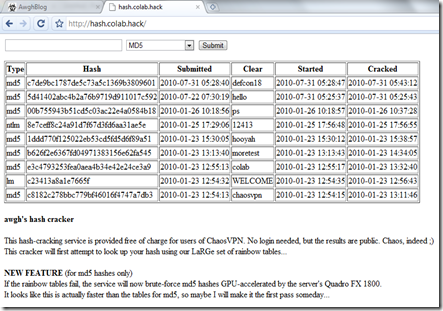
I’ve been hosting a Jabbercracky server with a large collection of rainbow tables on ChaosVPN since January, and I’ve recently done a bit of work packaging it as a Python module, so you can host your own cracking service with your own collection of rainbow tables!
On ChaosVPN, the service is available at: http://hash.colab.hack or http://10.100.23.1
The Jabbercracky module is currently being hosted on the Python Package Index, so all you need to do to install is:
1) easy_install jabbercracky
2) Go to the jabbercracky egg directory in site-packages and follow the installation instructions in INSTALL.txt
In future versions, Jabbercracky will live up to its name and also provide an XMPP-based interface, so you can crack hashes on your beefy hardware at home from the comfort of your mobile phone!
If you have any interest in participating in the development of Jabbercracky, please drop me a line!
Greetings to mc.fly and ryd and Defcon 18!
– awgh
This looks really cool. Looking forward to trying it.
How hard would it be to apply the GPU part of it to other applications, like video transformation?
Looks cool. Looking forward to trying it!
How hard would it be to apply the GPU processing to other applications, like video transcoding?
If you look at the Python code, you’ll see that this is really just a nice job control system for Python. It should be really easy to make calls to any command-line program, to collect the results, and to drive it with a simple web interface. There isn’t really even that much source (I like to be as concise as possible). You can basically just rip out the calls to the cracking programs and replace them with ffmpeg or mencoder calls or whatever and Bob’s your uncle.
just joined our space to chaosvpn
submitted some test hashes but they don’t seem to be getting cracked
I just discovered the problem, the “charset.txt” file vanished from /var/run/jabbercracky. This MUST be in the current working directory for the crack commands to work.
I’m not sure if this got killed when I did some system upgrades or if this is a bug in the Python egg…
If this is a problem for anyone else, you can fix it by copying the charset.txt file into /var/run/jabbercracky, like so:
cp /usr/lib64/python2.6/site-packages/jabbercracky-0.1.0-py2.6.egg/charset.txt /var/run/jabbercracky
I’m re-running your hashes now, we’ll see if anything else got broken by my system upgrades… Will keep you posted 🙂
– awgh
nice it got the easy ones i was testing, im pretty sure I entered the ntlm hashes right, hopefully those crack, now if these arent found in the tables it’ll kick over to the cuda cracking automatically?
Currently ONLY the MD5 hashes have a second-stage that uses the GPU. I am not aware of any NTLM-cracking programs that make use of the GPU, but as soon as one exists it would be easy to add in.
check out hashcat
http://hashcat.net/